Risk Assessment Tool

Multiple Frameworks
Our services encompass a variety of cybersecurity frameworks, offering you diverse options to align with your specific needs. Select the framework that best fits your organization’s security requirements and objectives: DiD Framework, NIST, CIS 8, CMMC 2.0, FTC Safeguard, CAN/CIOSC 104, HICP, etc.

Input Responses
- Provide your response for each control that will be included in the technical report at the conclusion of the assessment.

Remediation Plan
You can either use the recommended Read More >
You can either use the recommended remediation that was provided, or you can include your own personalized response.

Generate Reports
At the conclusion of the assessment Read More >
At the conclusion of the assessment, abbreviated reports can be prepared for members of the executive team as well as detailed reports for the technical team.

Control Reference
The controls include references to their appropriate Read More >
The controls include references to their appropriate positions within the security policies. Eliminate the controls that are unnecessary for the audit.

Reminders
Reminders can be configured Read More >
Reminders can be configured for when it is time to perform a reassessment.
Benefits
By conducting a cyber security risk assessment, the organization can proactively identify and address potential vulnerabilities before they can be exploited by attackers, helping to protect the organization and its assets from cyber threats.
Low cost
At a fraction of a cost that the large cyber security companies charge.
Know the Risks
Identify all risk associated with the organizations information technology systems.
Remediate
Remediate the risks posed by exposing the organization to potential threats.
Peace of mind
Knowing that the organization has minimized the risk gives all stakeholders peace of mind.
Applications
- Description for a key feature of this service. Description for a key
- Feature of this service. Lorem Ipsum. Description for a key feature of this service.
- Description for a key feature of this service. Description for a key feature of this service. Description for a key feature
- Key feature of this service. Description for a key feature of this service. Description for a key feature
- Service. Description for a key feature of this service.
- Service. Description for a key feature of this service.

Capabilities
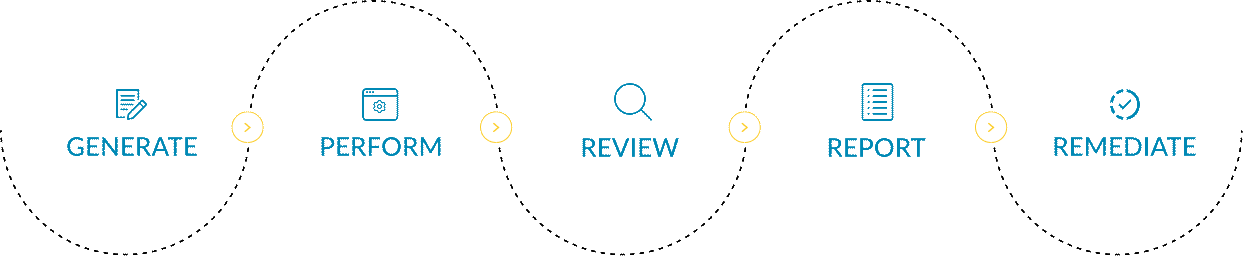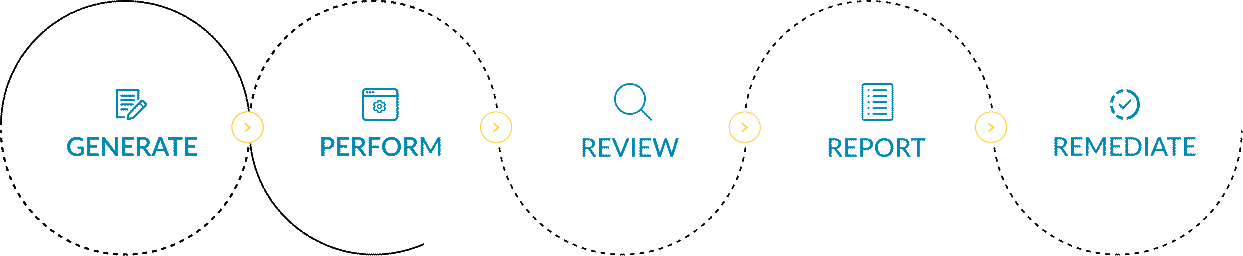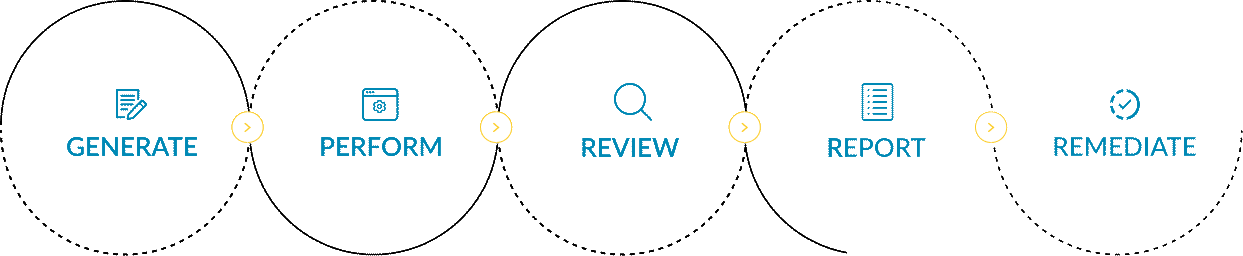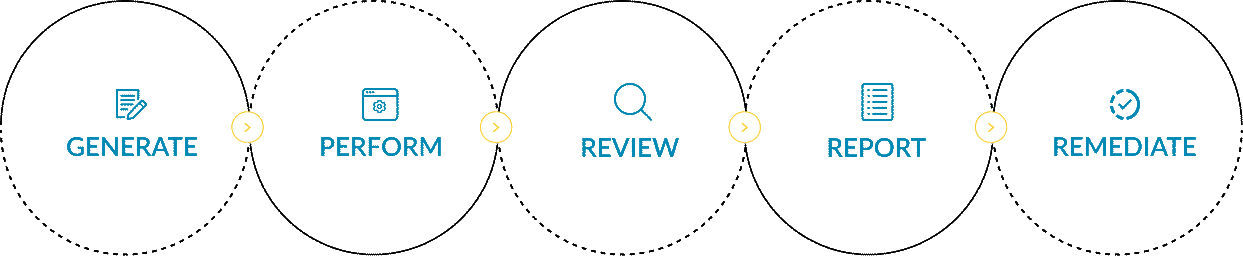
In the realm of cyber security audits, organizations follow a systematic process to ensure the integrity of their digital infrastructure. They commence by generating a new risk assessment, meticulously identifying potential vulnerabilities. Subsequently, they perform a thorough examination, review the findings, and swiftly report them to all stakeholders. Finally, armed with this knowledge, they strategize and formulate plans to efficiently remediate the identified vulnerabilities, bolstering their security measures.
Useful Resources
Cyber Auditing Best Practices
Compliance requirements affect many businesses today
The importance of a cybersecurity audit
Testimonials
an extra long review so we can see what 2 lines looks like here.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Lorem ipsum dolor sit amet, consectetur
Name Lastname, Company

an extra long review so we can see what 2 lines looks like here.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Lorem ipsum dolor sit amet, consectetur
Name Lastname, Company

an extra long review so we can see what 2 lines looks like here.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Lorem ipsum dolor sit amet, consectetur
Name Lastname, Company